Exploiter Becomes the Victim
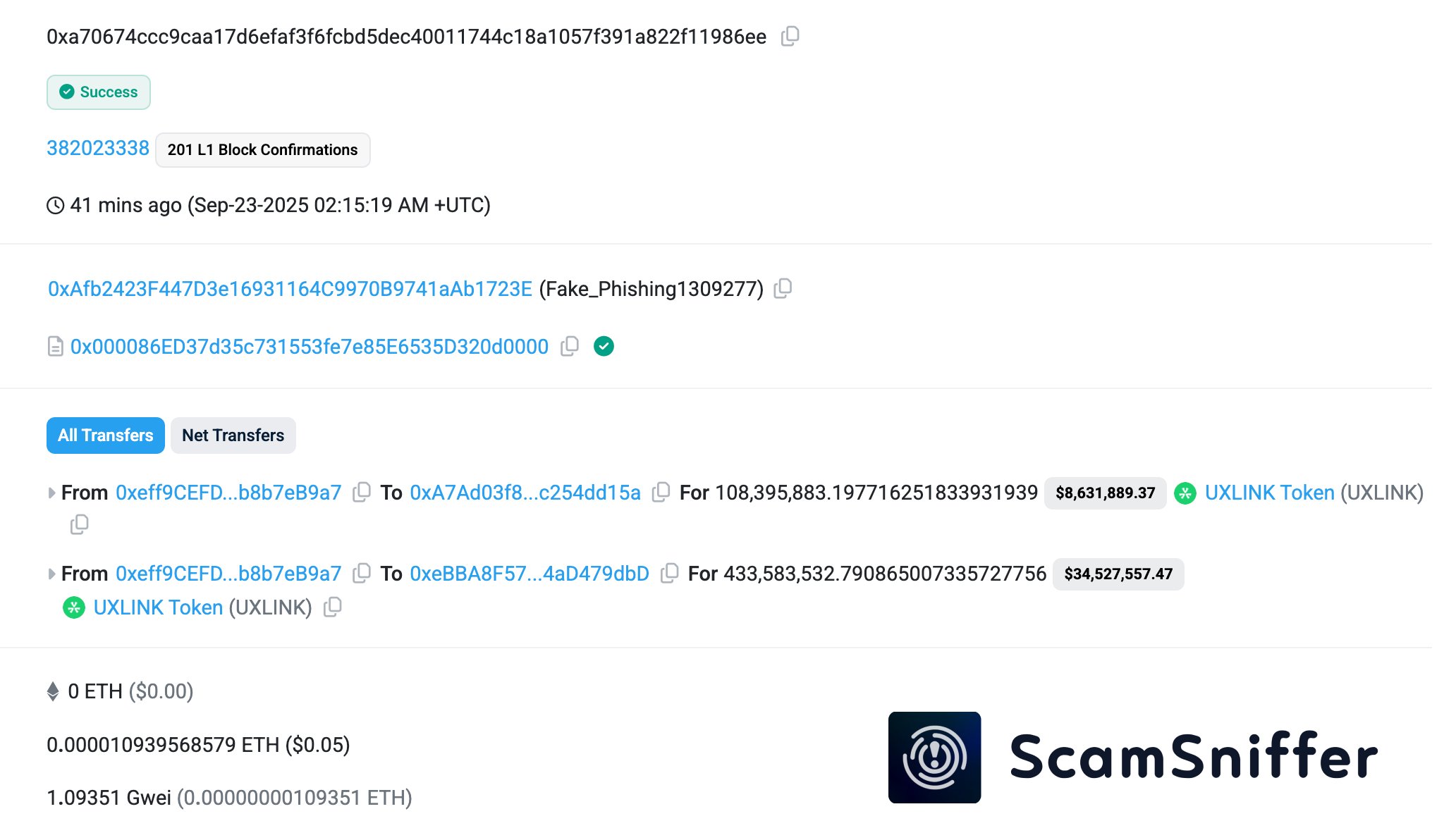
The ongoing UXLINK hack has taken an unusual twist. The exploiter behind the unauthorized minting of billions of tokens has fallen victim to a phishing attack, losing more than 542 million UXLINK tokens valued at over $43 million to addresses linked with the Inferno Drainer group.
Blockchain security firm ScamSniffer flagged the incident, noting that the wallet signed a malicious increaseAllowance approval. This enabled phishing contracts to automatically drain tokens into attacker-controlled wallets.
How the Phishing Attack Worked
According to SlowMist founder Yu Xian, the theft likely used ordinary authorization phishing methods. These techniques typically trick users, or in this case the exploiter, into unknowingly granting token-spending permissions.
The case shows a recurring danger in crypto: once a wallet is compromised or careless approvals are granted, funds can continue to be siphoned through secondary allowances and hidden authorizations.
Background: The Multi-Sig Breach
The phishing loss adds to UXLINK’s troubles. On Sept. 22, attackers exploited a delegateCall vulnerability in a multi-sig wallet, seizing administrator rights. That breach rerouted $11.3 million in ETH, WBTC, and stablecoins through Ethereum and Arbitrum.
Since then, the exploiter’s wallet has continued unauthorized minting of billions of UXLINK tokens, selling them on decentralized exchanges and bridging proceeds into ETH.
The project’s token value has dropped more than 70% since the first breach, erasing nearly $70 million in market capitalization.
Response and Recovery Efforts
In response, UXLINK developers announced a token swap to restore supply integrity and freeze compromised tokens. They are also working with centralized exchanges to suspend deposits and flag suspicious wallets.
Whether this recovery plan can restore trust is uncertain. The fact that even the exploiter was compromised by Inferno Drainer highlights how chaotic these exploit scenarios can become.
Broader Implications
The UXLINK case illustrates two key risks in the DeFi ecosystem:
-
Bridge and wallet vulnerabilities remain prime targets for attackers.
-
Phishing campaigns exploit already compromised wallets for further losses.
Security researchers warn that such cascading compromises may become more common as exploiters themselves operate in high-risk environments without strong security practices.